Governance, Risk and Compliance
RSA ARCHER
IT & Security Risk Management
Business context
With over 15 years of Enterprise IT exposure and excellence, we ensure the entire process of defining business continuity plans and deploying IT disaster recover solutions for large organizations.
Building datacenter IT infrastructure, deploying and configuring complex business applications (ERP, CRM, ECM) – all of these are represented by our professional team.
The GRC component came naturally as an added layer to the existing services offered. Our competences lie in RSA Archer GRC, SAP GRC (Access Control) and Microsoft GRC (O365 E5).
RSA Archer Installation, Configuration and upgrades
RSA Archer
Platform Administration
RSA Archer
Customization & Optimizations
RSA Archer Installation, Configuration and upgrades.
Deploying RSA Archer GRC requires deep understanding of existing IT infrastructure, business processes, satellite systems and applications.
Our enterprise background and experience gives a real advantages to customers who want to leverage it during the design and implementation phases.
We asses existing IT Infrastructure and design RSA Archer technical solution carefully considering all components: sizing, networking, firewalls, authentication and authorization, segregation between various instances.
We configure and customize the out of the box RSA Archer Solutions to the needs of the customer while referring to the best practices in the industry. Always.
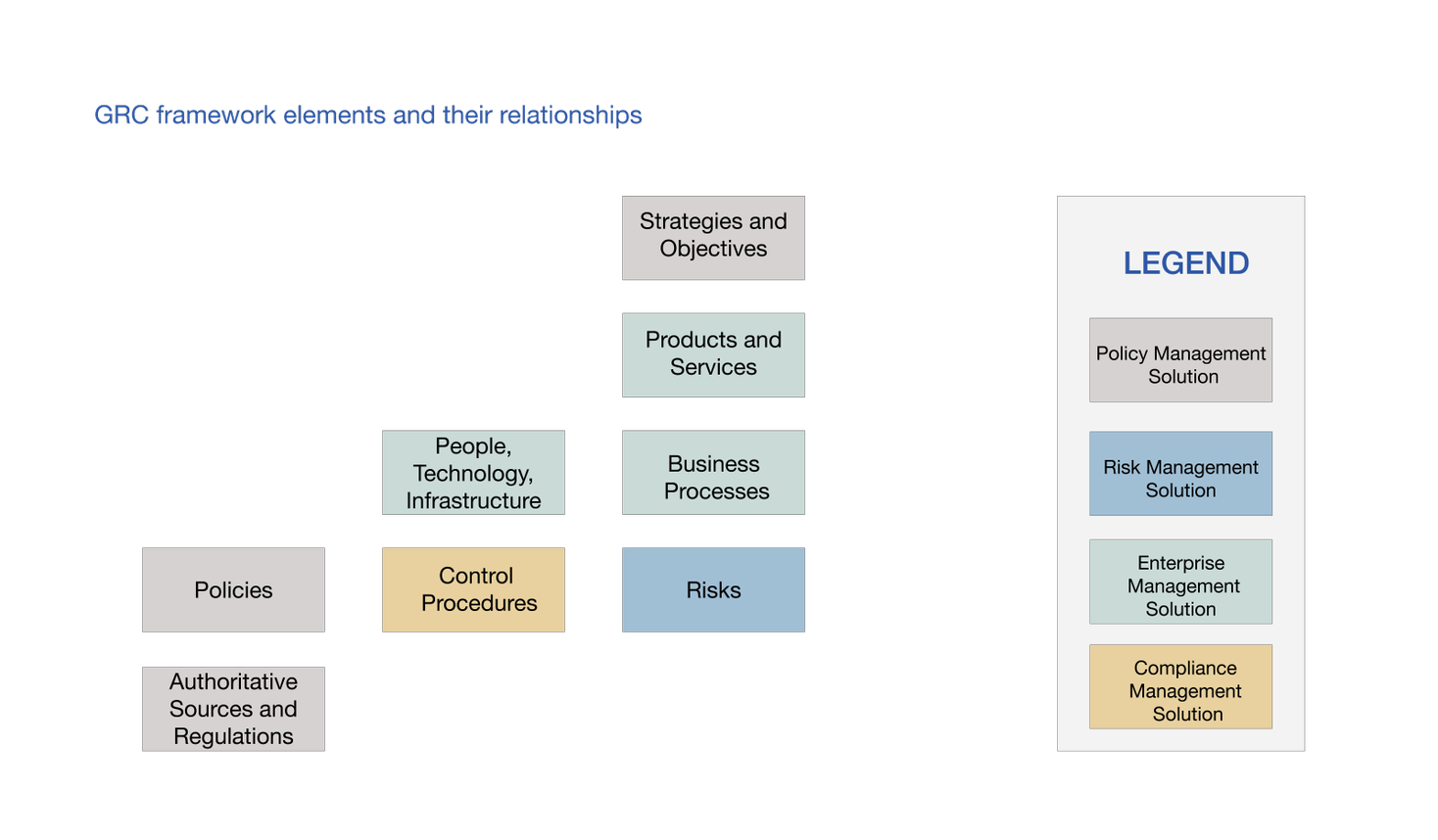
Our consultants set up, implement and visualize data and relationships to the true benefit of RSA Archer GRC advantages identifying preferential data required, normalizing and establishing automated daily feeds for consistency and freshness.
We help and assist your company in Integrating the RSA platform with external systems, configuring automatic data analysis against defined controls, triggering workflow actions to support the processes mapped in Archer, designing custom reports in Archer or externally.
RSA Archer GRC serves as an aggregation hub for consolidation of governance risk and compliance information.
Solution configuration
Risk Management
- Map IT components and applications to business processes, define questionnaires to collect risk metrics and dependencies
Business resilience
- Define assets, controls, questionnaires, the risk to decide the necessity of the business processes.
- Integrate incident and crisis response, develop detailed business continuity and disaster recovery plans
Policy Management
- Advice necessary policies, design them and manage controls, risks, assessments, and deficiencies.
- We help the mapping of control standards with policies (various teams may have different interpretations; level the subjective interpretations and find the common denominator)
- Threat Management
- Compliance Management
- Enterprise Management
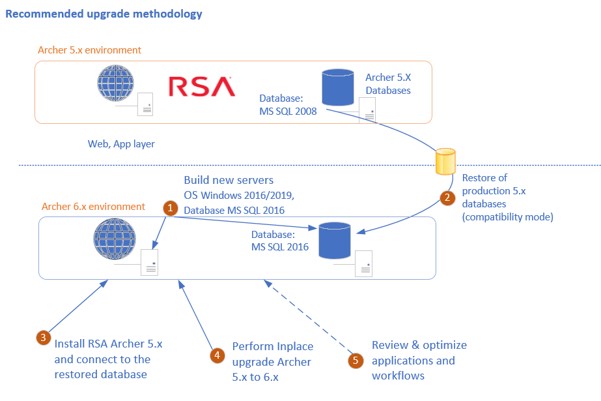
Platform Upgrades
- Upgrade RSA Archer from v5.0 to 6.x (in-place, a new platform with data migration, hybrid).
- Data import from old instance to the new one.
- Feeds reconfiguration.
RSA Archer Platform Administration
We offer a fully managed platform management service.
Expertware assigns a team dedicated to each RSA Archer platform implementation and ensures that customer's particular processes and IT landscapes are well documented and monitored 24/7.
Standard activities part of the service agreement
- Managing existing data feed loads, adjusting and remediating where it needs.
- Design, develop and run more data feeds (preferential data feeds, IT risk feeds, QA feeds, Process, and Policy feeds, etc.)
- Administration for authorization: per application, per field, enforce/break inheritance, validate controls so we grant business users access to specific data records and fields.
- Monitoring and remediation for RSA Archer platform services, performance, warning & errors.
- Ensure report data accuracy (freshness) and workflow actions completion.
- Design, develop solutions based on requests from Business Owners (authorization, data imports, small changes in applications).
- Define and configure new reports, questionnaires (to map business processes with risks), forms, workflows.
- Troubleshooting, investigating and correcting data feed errors.
RSA Archer Customization & Optimizations
Where is a need we can assist our customers to audit and optimize their implementations.
We've seen many times deployments where the pain-point was generated by a wrongly defined field, a missing data feed or an incomplete process mapping. The success of a RSA Archer GRC implementation has a strong dependency on the correct definitional of data relationships and authorizations.
We can bring to our customers our experience in mapping the business processes to ideal set of data fields, records and workflows.
Together we assess and identify if existing referential data and custom fields have been optimally defined. If we identify missing dependencies or wrongly assigned fields Expertware proposes remediation plans to update and improve the solutions (review / define calculated fields, records, applications, inheritance and field level security settings).
Make use of advanced features like cross reference between various RSA Archer data fields.
Activities performed based on audit findings:
- Harness the power of Advanced Business Workflow to define and automate business processes for streamlining content management, tasks triggering, status actions, approvals.
- Use Application Builder to map business requirements in optimal field types.
- Develop or customize workspaces, applications, solutions, authorizations.
- Design and develop custom reports, dashboards, workspaces.
- Develop and optimize data feed integrations with other sources (Qualys, Syslogs, LDAP, ERP systems, QA systems, ITSM).
- Use Workflow Process Designer to map business processes to custom workflows (checks, statuses, triggers, automated actions), define advanced workflow nodes.
Our added value
- Strong knowledge about the infrastructure and application relationships.
- Deep understanding of data points required to be evaluated for Vulnerability Management risk analysis
- Capability to correctly qualify risks considering the existing infrastructure and processes interrelations.
- Strong understanding of the risk definition: top to bottom, bottom to top and ability to advise the customers in the process of defining them.
- Broad business processes understanding: financial processes, logistics, incident and request management, customer services, sales and distribution, etc.
- Capability to optimally map Policies to instances: per technology, per applications, per environment (DEV, TST, UAT)
- Experience to map Business Processes to Applications and controls: multiple asset items form an application which is influencing one or more business processes.
- Capability to qualify the vulnerabilities based on the technical landscape: not all systems are equals.
- Capability to advise the customers defining and calculating risk profiles.

Copyright © 2020 - All Right Reserved.