Business context
Businesses for many years have sought to protect end point devices using antivirus and antimalware software that performed regular scans based on lists of known threats. These solutions took no account of the activities of employees using the devices or patterns of activity across endpoints.
These passive approaches required different solutions on different endpoints and often completely missed new threats such as ransomware until fingerprints could be developed. The days of passive antivirus protection based on static lists are now over.
True end-point protection requires active monitoring with the responsiveness of AI, real time threat intelligence and responses that understand the complexity of a modern IT estate and recognise that the end point is just one element of an interconnected architecture.s
Our solution
Expertware in conjunction with our specialist EDR partners can provide a managed End point detection and response solution that utilises best of breed tools coupled to an integrated operations centre to quickly detect and respond to any threats on any platform while your team get on with the day job.
Advanced Security incident protocols are used to assess threats and take action based not only on known fingerprints but also based on deviations from standard traffic flows, unusual activity, and pro-active analysis. The majority of endpoints can be protected from Laptops and PCs to Tablets, Smartphones, and IOT devices.
A centralised deployment model can be provided utilising either your own standard software deployment solutions or triggered by our access control solution to ensure all connected devices are fully protected
Our subscription-based services are charged per device and include monthly reports, Operations centre monitoring and automated response workflows and alerts so that you are always in the picture and aware of potential issues.
A range of Solutions to suit any need
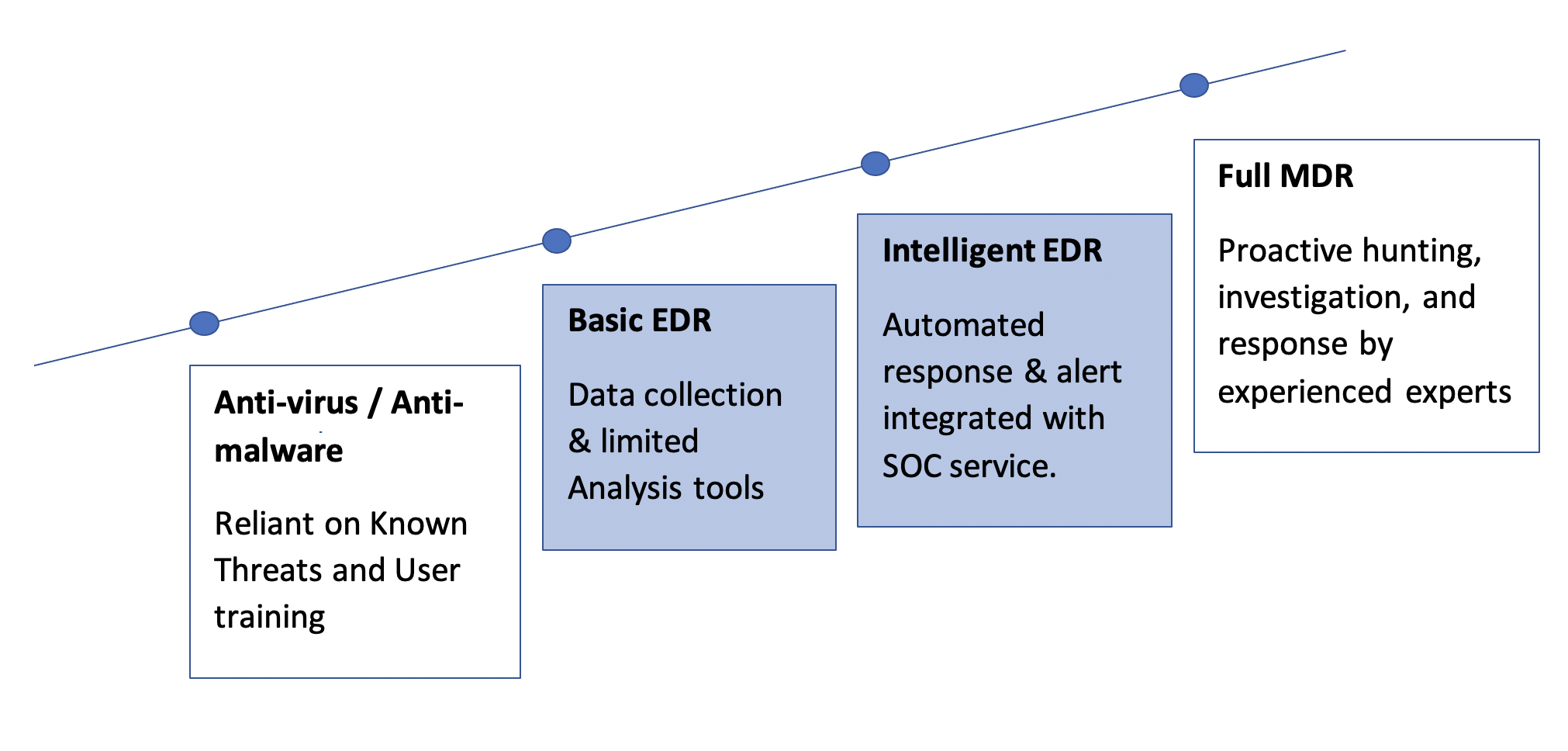
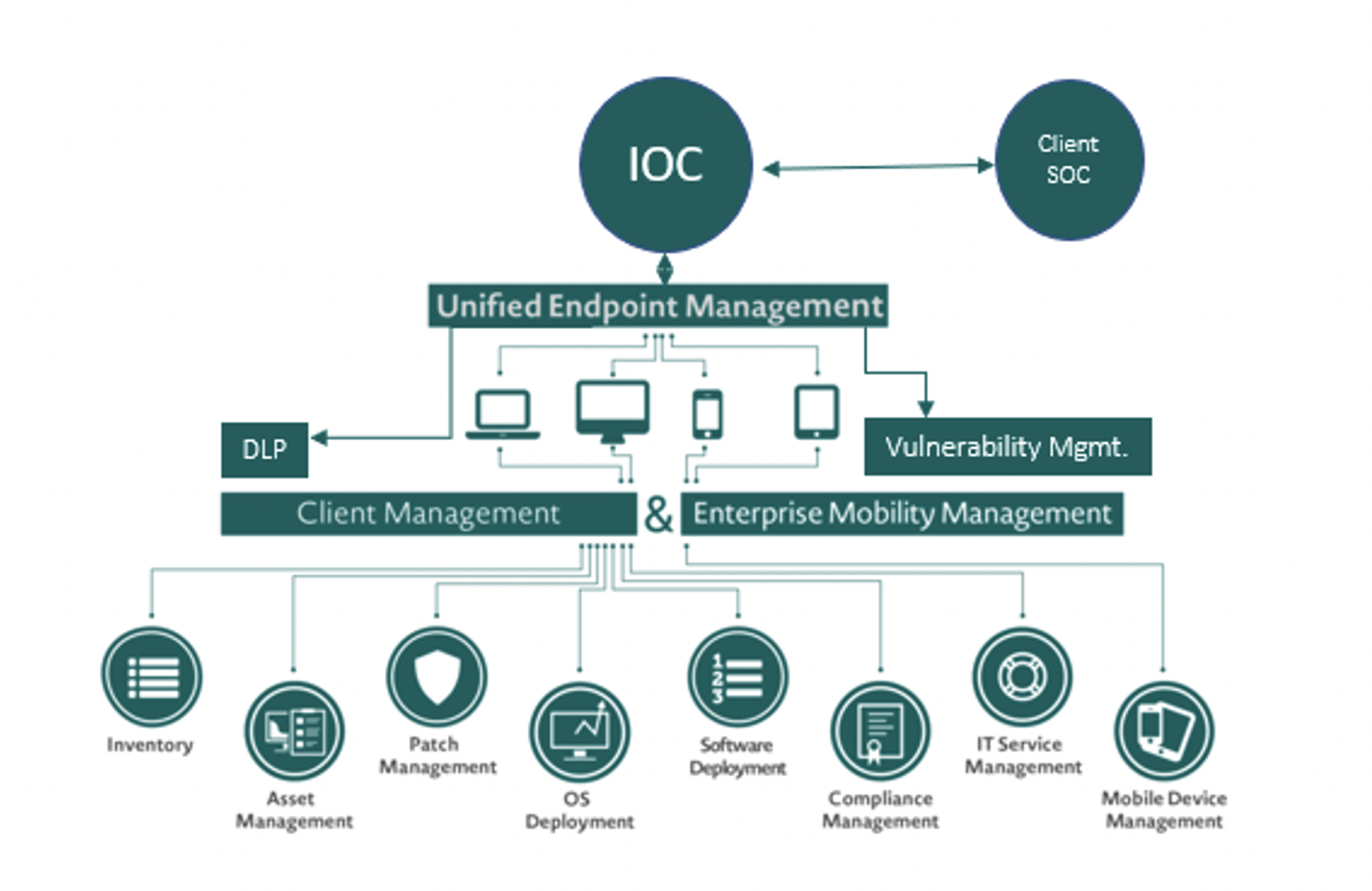
Part of the Expertware End-point management solution
Our Experience
With over 15 years of experience in the field of IT architecture and managed services, we are confident that we can offer to our customers a team with very strong technical knowledge and a deep understanding of the IT architecture models and solutions in place. Our people will become a trusted part of your team.
For each customer, there is a solution architect supervising the activities of the operation team guaranteeing a continuous review and optimization for monitoring and alerts, automated response flows ensure rapid responses but always under the guidance and oversight of our expert technicians.
We aim to provide state-of-the-art SIEM services to our customers so that they can continue their business safe in the knowledge that strong protection is in place.
Integrated Solutions
- Integrated 24*7 operation centre
- Analysis of IT architecture design to select the best SIEM solution and processes to meet your business objectives and needs.
- End to end the collection of monitoring data, events, and alerts.
- Human and AI analysis of event data.
- Real-time global threat searches and patch automation.
- Operational management for KPIs and executive dashboards.
Our Added Value
- One-stop-shop for configuration, monitoring, analysis, and event management.
- Strong competences, certified engineers (SQL Silver Data Platform, T-SQL/SSRS/OLAP, Business Objects, SAP BW, Elastic).
- Can-do attitude, accepting and completing difficult challenges.
- Cost efficiency combining near shore with onsite resources and eliminating overlapping roles through our integrated operations centre initiative.

Copyright © 2020 - All Right Reserved.