Network Access Control
Business context
Many Organisations rely on device-based password access controls or employee policies to protect the basic security of their business. Applications are housed within a single core network accessed by all employees either directly or over a VPN or remote access link.
This architecture whilst workable leaves the organisation vulnerable to attacks either from external threats or from internal policy breaches. Once access is obtained all systems are vulnerable.
But there is another way!
Intelligent access controls that segregate systems based on business function and recognise valid access requests for each can significantly reduce risk.
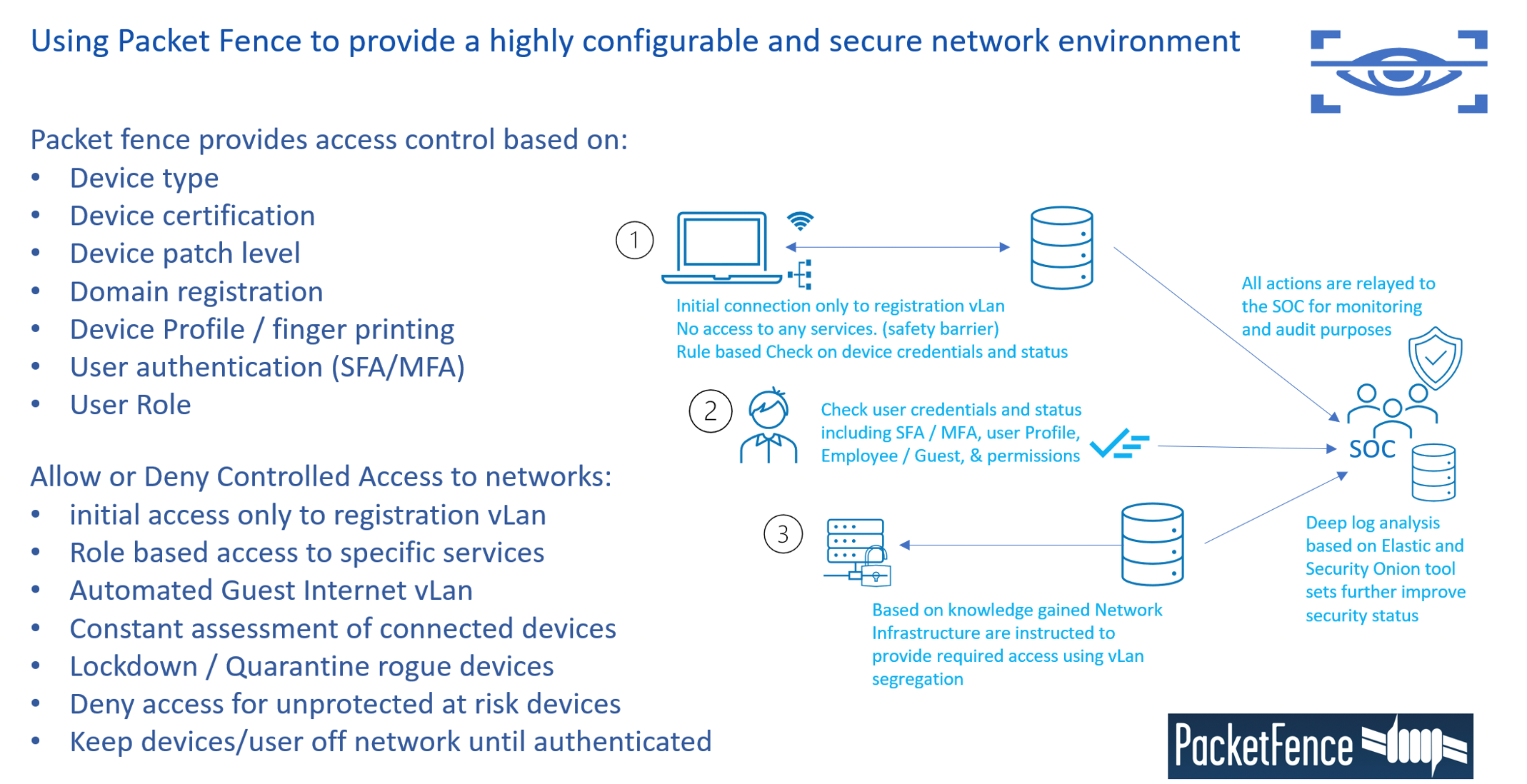
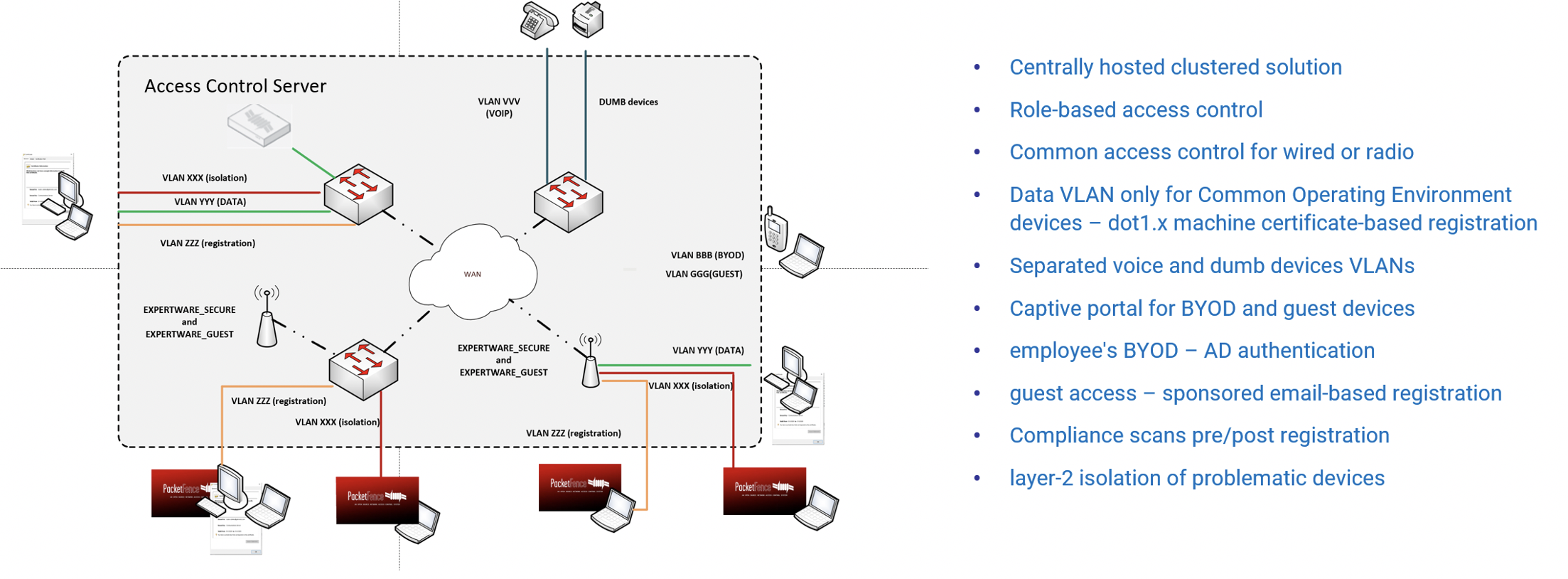
Expertware partners with Packet Fence to create a tailored access management solution for each client. Systems are separated into different VLANS and a centrally managed solution vets all devices and users as they attempt to connect to either wired or wireless networks. Access is granted based on device status, SW patch level, device credentials, User profile, or Sponsored access approval.
- Systems Segregated using Virtual networks.
- End point devices must be up to date and known in order to gain access.
- Compliance scans pre/post registration.
- Individual User profiles define what can be accessed and when.
- Limited Guest access can be granted by a sponsoring employee through workflow.
- Full active Directory integration.
- Control BYOD and guest device access.
- Device Isolation solution for problematic devices.
- Reporting and utilisation via a management portal.
Expertware can provide Packet fence as a standalone solution or as part of an Integrated security model with Packet Fence managed as part of its Integrated Operations Centre model further enhancing and expanding its capabilities and policy enforcement functionality.
Our Solution
Our Experience
With over 15 years of experience in the field of IT architecture and managed services, we are confident that we can offer to our customers a team with very strong technical knowledge and a deep understanding of the IT architecture models and solutions in place.
Our people will become a trusted part of your team. For each customer, there is a solution architect supervising the activities of the operation team guaranteeing a continuous review and optimization for monitoring and alerts, automated response flows ensure rapid responses but always under the guidance and oversight of our expert technicians.
We aim to provide state-of-the-art SIEM services to our customers so that they can continue their business safe in the knowledge that strong protection is in place.
Integrated Solutions
- Integrated 24*7 operation centre.
- Analysis of IT architecture design to select the best SIEM solution and processes to meet your business objectives and needs.
- End to end the collection of monitoring data, events, and alerts.
- Human and AI analysis of event data.
- Real-time global threat searches and patch automation.
- Operational management for KPIs and executive dashboards.
Our Added Value
- One-stop-shop for configuration, monitoring, analysis, and event management.
- Strong competences, certified engineers (SQL Silver Data Platform, T-SQL/SSRS/OLAP, Business Objects, SAP BW, Elastic).
- Can-do attitude, accepting and completing difficult challenges.
- Cost efficiency combining near shore with onsite resources and eliminating overlapping roles through our integrated operations centre initiative.

Copyright © 2020 - All Right Reserved.